Security Certificate Management for Tactical Edge networks
Date
In an earlier blog, “The future of the Tactical Edge“, we noted that personnel could be in highly stressed environments. With so much going on in the foreground, Communications Managers can do without the stress of manually configuring network infrastructure and repeatedly applying digital credentials for secure network communications. With this in mind, Klas created Blackrock, a comprehensive software solution for managing, automating, and monitoring network infrastructure.
In the latest Blackrock release (from version 2.1), Klas has integrated Public Key Infrastructure (PKI) management to configure network communications for the Tactical Edge securely. The newest release natively interfaces to a range of components approved under the list of NSA Commercial Solutions for Classified (CSfC), including two approved Certificate Authorities (CA).
PKI Challenges
PKI is critical to protecting data online, allowing us to share data over public networks such as the internet cryptographically. PKI is used to verify that the sender of the data is legitimate and to ensure the privacy of the message sent between two points on the network.
Although PKI is the most trusted way of encrypting network traffic, it is complex for those with minimal IT experience, especially those operating in highly charged environments.
Software management for PKI
The NSA CSfC Mobile Access (MA) Capability Package (CP)¹ outlines the architecture to facilitate mobile access to classified red networks. In the CP, the CSfC deployment consists of two distinct security enclaves Black/Grey and Grey/Red. The CP outlines the need for the data to be encrypted twice with separate management services.
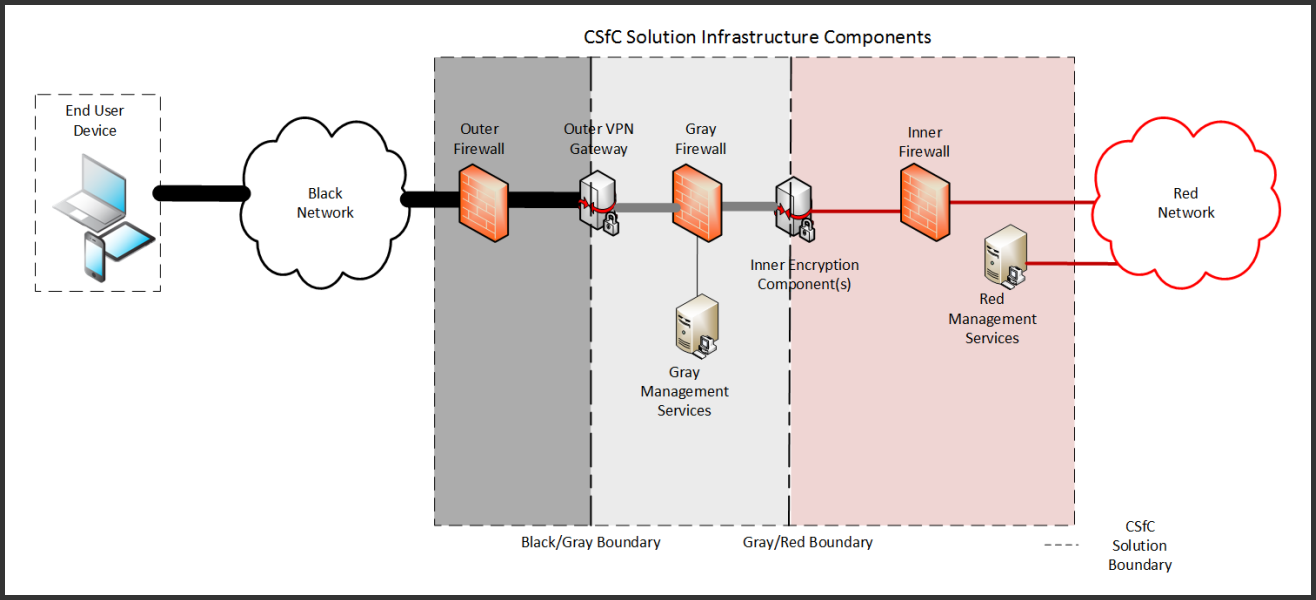
Figure 1: Overview of Mobile Access Solution (source NSA, see Resources)
Setting up two enclaves by hand is time-consuming. Furthermore, when the requirement is for multiple mobile access nodes at the tactical edge, the challenge is to avoid making mistakes when configuring manually. The alternative is to use software automation to do the configuration.
Advantages of Software Automation
Software automation has many advantages; there is a significant reduction in effort and time, it minimizes errors, but more importantly, it is far more secure. As there are no humans in the middle of the process – signing in and out of each device, saving digital certificates on 3rd party machines, rotating digital certificates, etc.
Per figure 1 above, Blackrock acts as the Grey Management Service, and a separate Blackrock instance serves as the Red Management Services.
Simplified PKI Management
Introduction
Blackrock manages any IP networked device that supports an API or SSH secure remote access. We have pre-configured Blackrock to manage two Cisco IOS-enabled devices, known as HOSTS, in Blackrock. We can also see that the IPsec tunnel is down between the endpoints.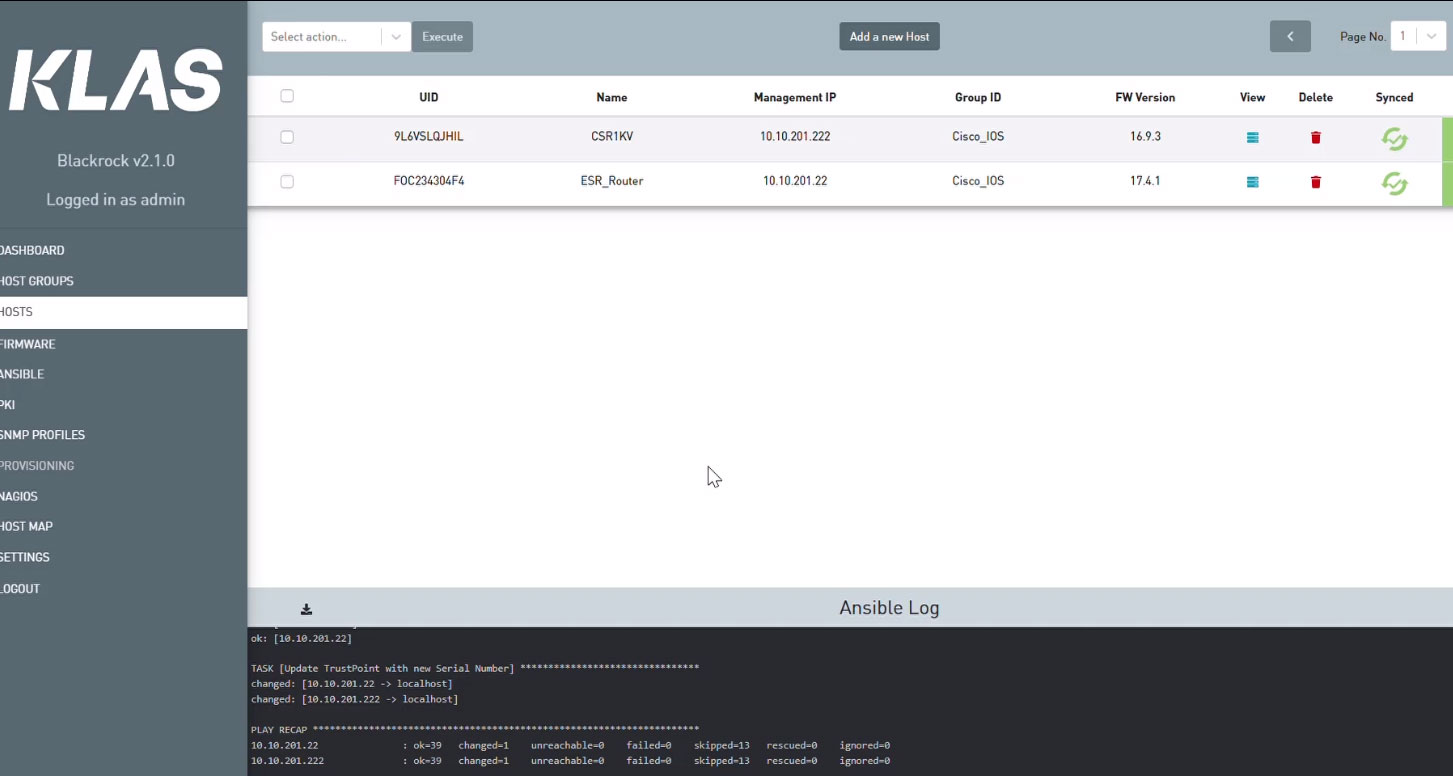
Step1 – Add Certificate Authority (CA) Configuration
Blackrock supports NIAP-approved CA e.g. ISC Certagent and PrimeKey EJBCA. Shown in the short video is the CA configuration. Point to the networked CA, add credentials and upload the CA root certificate. Within seconds the CA is available for use in the enclave.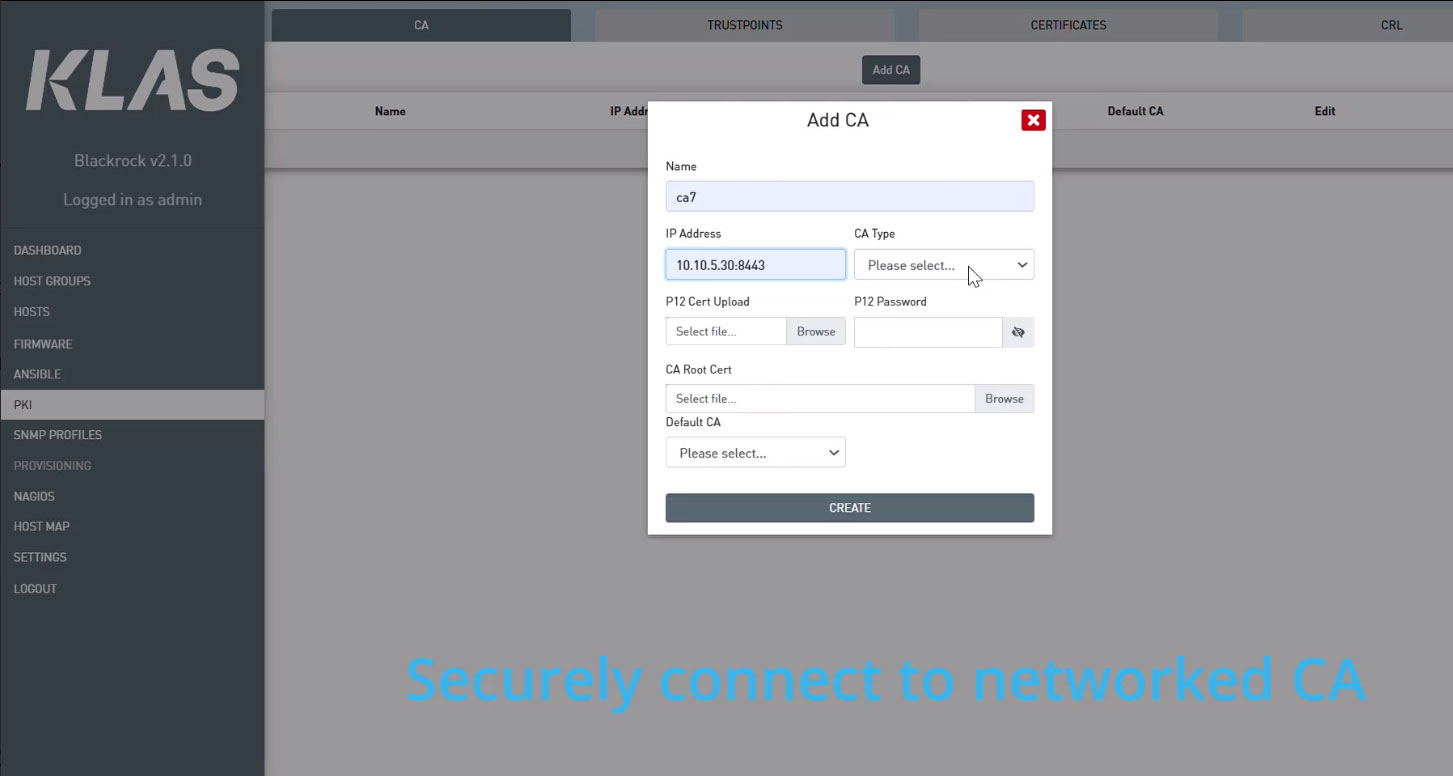
Step2 – Add VPN Gateway Configuration
The next step is to generate a Certificate Signing Request (CSR) for both sides of the IPsec tunnel. Trustpoints are the containers on the VPN gateway under management that hold the identity and certificates. Select the VPN gateway host, the CA, and add the Key types and sizes.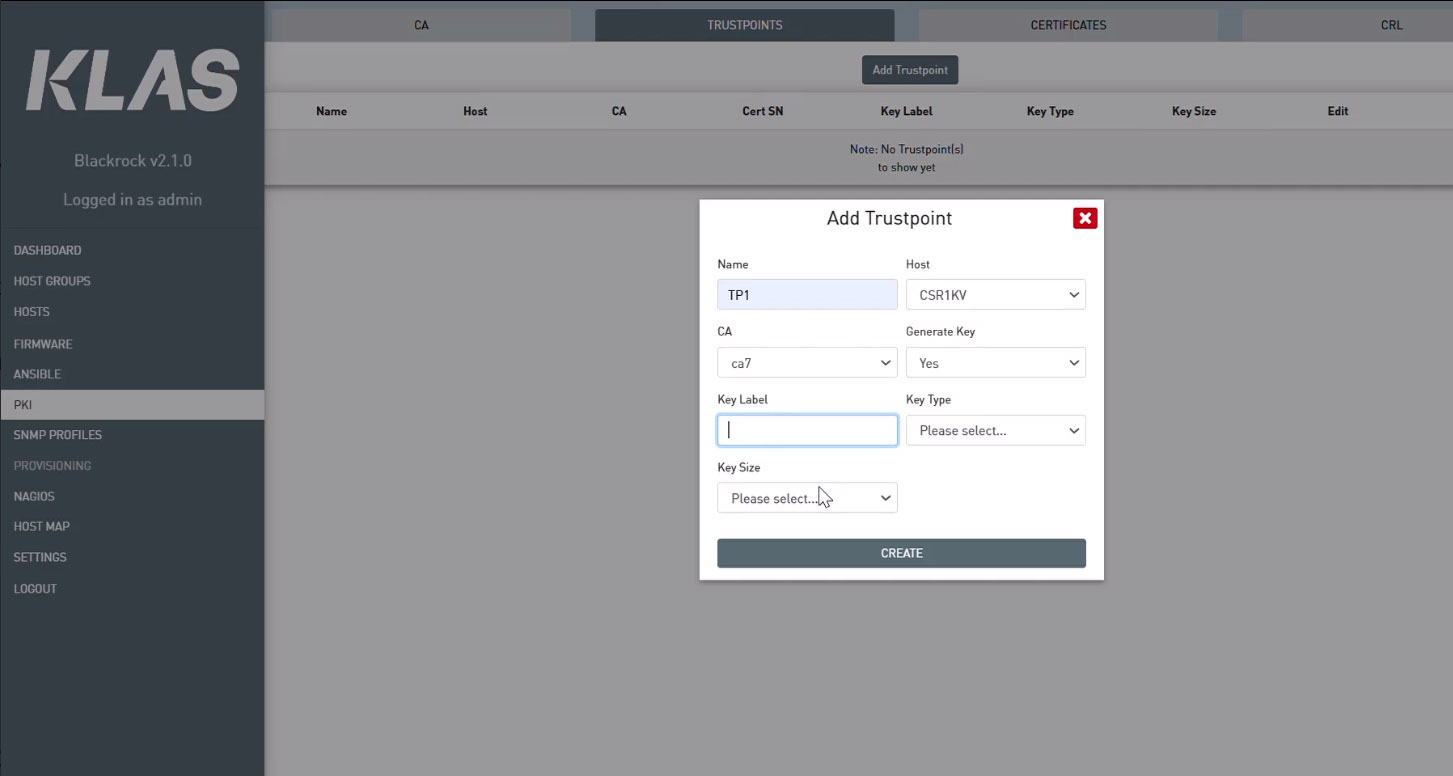
Step3 – Execute PKI certificate enrollment
Select the HOSTS to be updated and execute the PKI enrollment function. Sit back and relax while Blackrock takes care of the certificate creation and pushes to the VPN gateways. Upon completion, a synopsis of the certificate’s details is available in Blackrock.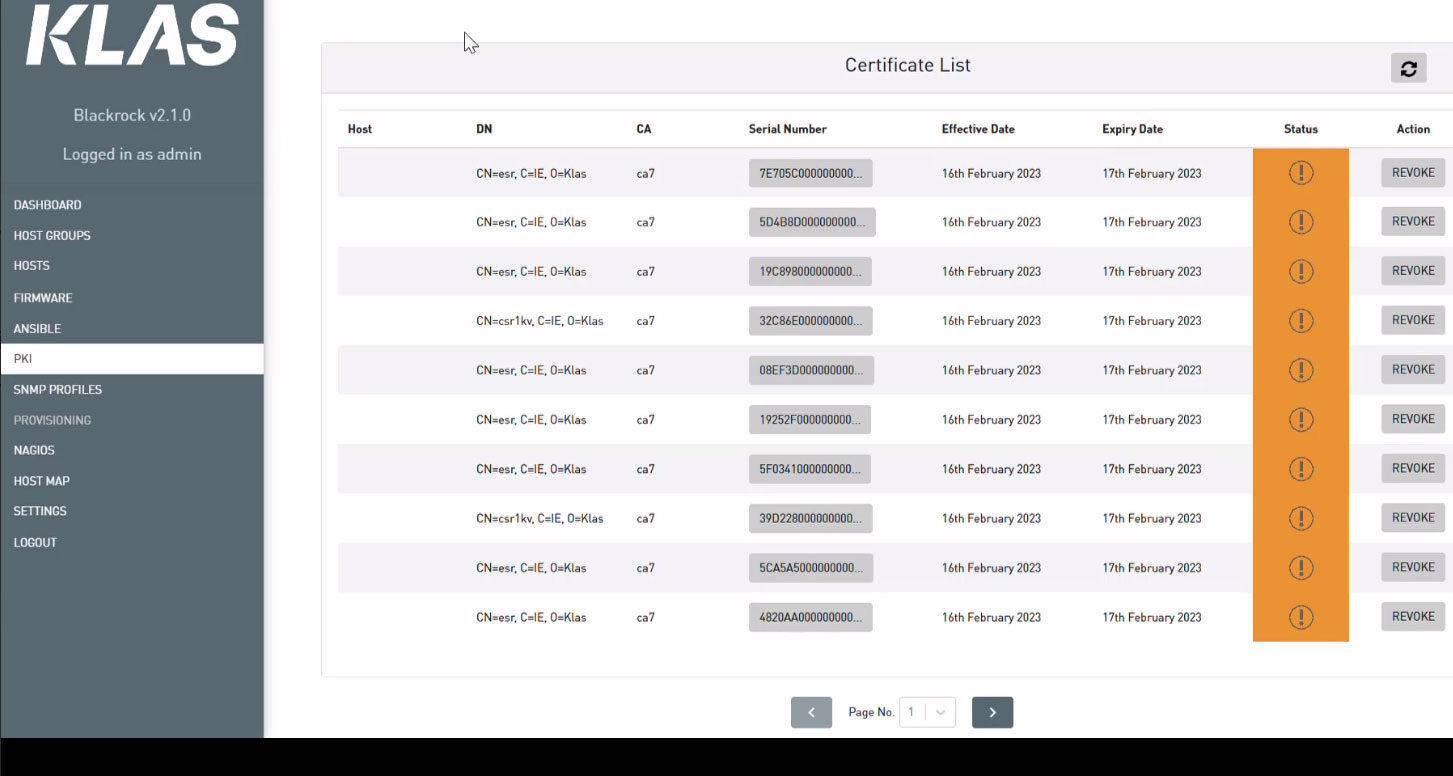
Step4 – Validate IPsec Tunnel as operational on the headend
Blackrock integrated monitoring tools allow users to see the status of the IPsec tunnel quickly. After several seconds the tunnel will go green, showing a secure connection.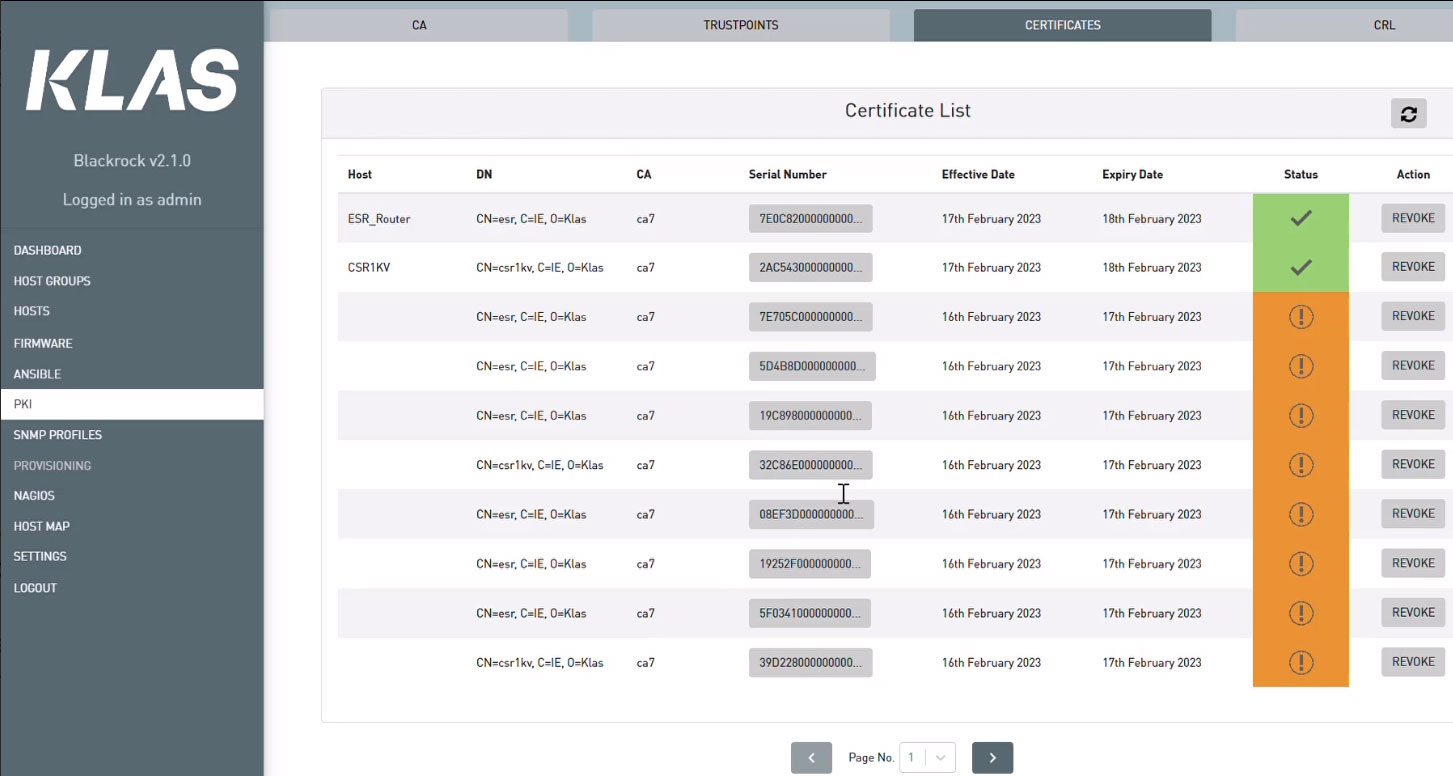
PKI Certification Rotation
Blackrock can detect and rotate certificates expiring, saving the hassle of continuously checking to see when a certificate is about to expire. Saving valuable time and ensuring critical secure communications are always operational at the Tactical Edge.
Intermittent Connectivity
Connectivity can never be guaranteed, and in the event of an outage, Blackrock will automatically attempt to rollover the certificate every hour. If connectivity is restored before the hour, administrators can manually generate new certificates. Similarly, in the event of the need to reconfigure/reassign certificates, administrators can manually enroll new certificates.
Why choose Blackrock?
Blackrock abstracts the complexity of networked devices and managing digital certificates, making it more reliable and easier to manage scaled Tactical Edge deployments. With Blackrock you get:
- A holistic pane of management: a modern secure portal to manage and monitor all networked device configurations and digital certificates.
- Greater security: automated provisioning of network devices and security, requiring minimal human intervention.
- Faster Deployments: pre-built support for a range of network devices and flexibility to add components approved under the list of NSA CSfC for streamlined deployment.
