For convenience, modern servers such as VoyagerVM (3.0 and 4.0) and VoyagerHPC come with an embedded Baseboard Management Controller (BMC) processor and an associated firmware stack such as OpenBMC. BMC facilitates the ease of access and management of the server’s resources, including the ability to install an OS on the central processing unit.
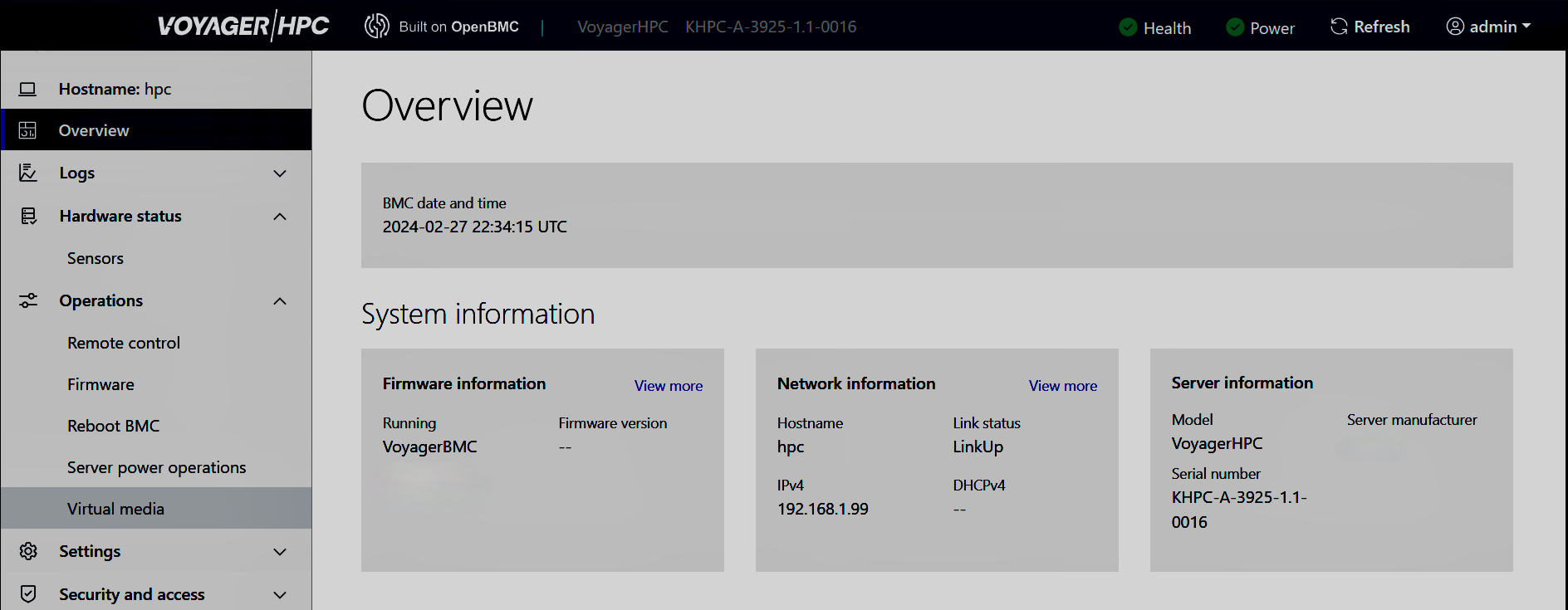
Figure 1: OpenBMC graphical user interface allows IT admins to configure and manage compute devices from anywhere.
A key use case for BMC is to enable remote IT admin capabilities without the need to attach a physical keyboard, mouse, or video display, often referred to as KVM. A further advantage is that the IT admin can remotely manage the server over Ethernet, without the need to be physically present.

Figure 2: VoyagerVM 4.0 – OpenBMC is accessible via a dedicated RJ45 ethernet management interface.
Anduril maintained OpenBMC
As is the case with any networked device, BMC and OpenBMC are legitimate targets for hackers to gain a backdoor entry into the device and the organization’s network. To ensure that BMC and OpenBMC are not exploitable, Anduril internally maintains its own version of OpenBMC.
The OpenBMC team at Anduril continuously monitors for the latest cybersecurity threats and common vulnerabilities and exploits (CVEs). When a cybersecurity threat is identified, the team will issue a patch update to protect our customers as soon as possible. At the same time, other vendors are reliant on the open-source community for patch updates. This results in days or weeks of an open security exposure in the network.
A rugged cybersecurity framework built on OpenBMC
The core pillars of a robust cybersecurity framework include the ability to identify, protect and detect. While we have touched on identification and protection, detection requires the ability to monitor the device continuously.
To assist our customers in delivering a robust cybersecurity framework, the Anduril maintained OpenBMC supports the DMTF Redfish® standard. An application programmable interface (API) for simple and secure management of the tactical compute edge at scale.
With Redfish, customers can continuously query the device to understand its state, running software versions, and gather sensor information for more robust analysis of performance. Additionally, with Redfish, customers can automate patch updates for devices, creating a more robust and secure operational environment.
Secure edge operations with OpenBMC
The following highlights three standard security best practices that are easy to implement with Anduril maintained OpenBMC running on the Voyager compute platforms. All without the need for KVM or being beside the device:
- Secure IT access: Secure authorization and access with role-based access controls.
- Secure BIOS and boot: Password protect the device BIOS to prevent users from circumventing security policies. Leverage TPM 2.0 and secure boot to prevent unathorized software loading.
- Automated patch updates: Over the Redfish API, monitor devices and sensors at scale, securely push patches and updates as and when required.
In Summary
A robust cybersecurity framework for edge computing starts with a trusted device and its associated firmware stack, which is continuously updated to mitigate the latest cybersecurity vulnerabilities and exposures. With Anduril’s internally maintained OpenBMC you can be confident that a team of experts is always looking to identify and will, as soon as possible, issue a patch to keep Voyager compute safe against cyber threats.
[Click to see the full range of Voyager rugged compute platforms.]